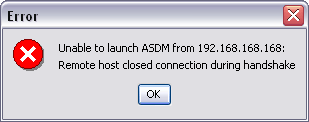
By default, Cisco ASA-assigned remote access IPSec VPN users will not be able to manage the firewall using Adaptive Security Device Manager (ASDM). Attempts to connect to the ASA firewall using ASDM will fail, and will return the error message "Remote host closed connection during handshake." Further, the ASA will create a log entry stating "flow terminated by tcp intercept."

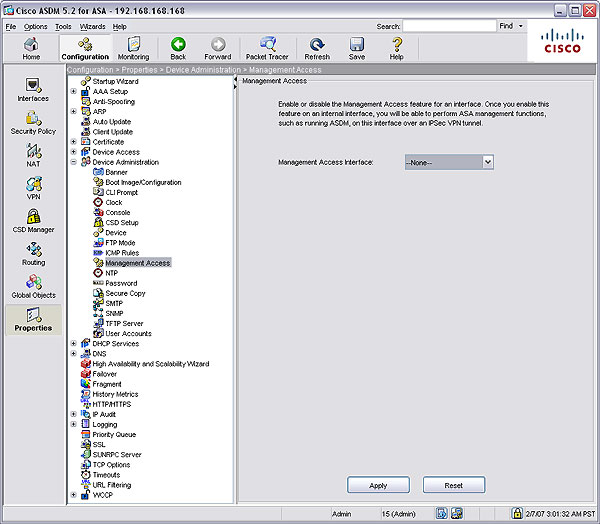
To allow remote ASDM access, configure the ASA to allow management access on an interface that is not assigned the lowest security level (i.e. the Outside interface). The following procedures show how to allow ASA ASDM access on the Inside interface, using either the command line interface (CLI) or the ASDM GUI.
Method 1: Command Line Interface (CLI)
ciscoasa# config terminal ciscoasa(config)# management-access inside ciscoasa(config)# end ciscoasa# |
Method 2: ASDM Graphical User Interface (GUI)
Do the following from the ASDM GUI: